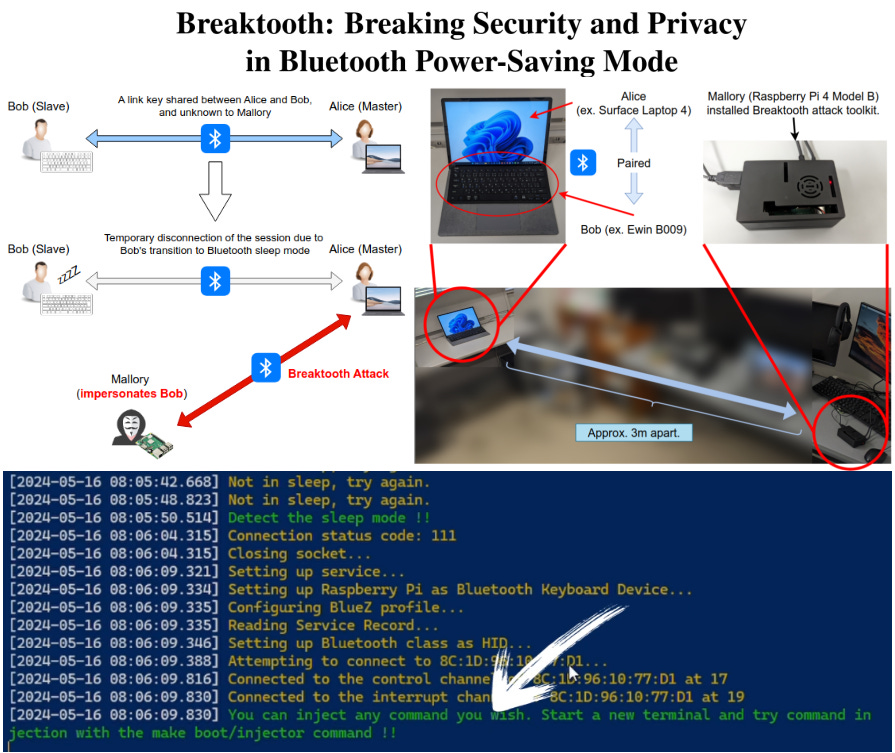
Serious vulnerability in Bluetooth protocol: once a device goes to sleep, its session can be hijacked by attacker. 🔵၊၊||၊🧲😴
Security researchers Keiichiro Kimura, Hiroki Kuzuno, Yoshiaki Shiraishi, and Masakatu Morii from Kobe University (Japan) published their research on Bluetooth power-saving mode and discovered that once a device (slave) enters sleep mode, it can be easily impersonated and the session can be hijacked. They named the attack: Breaktooth.
No exotic hardware, no firmware hacking, no special permissions needed. The attacker simply sends echo requests (l2ping) to the target’s Bluetooth address and observes how it responds. If the victim device stops responding, it’s ready for attack.
Super interesting and deadly attack. And to my understanding, it will not be very easy to fix.
Read the paper, check the code, and if you find it interesting, consider sharing this research with your colleagues and friends!
Thanks. :)
More details:
Breaktooth: Breaking Security and Privacy in Bluetooth Power-Saving Mode [PDF]: https://eprint.iacr.org/2024/900
Website: https://breaktooth.github.io/
PoC [Google Drive]: https://drive.google.com/file/d/13SPIGO1AuhxTk-s1RFkENd7T5qWp2YbN/view