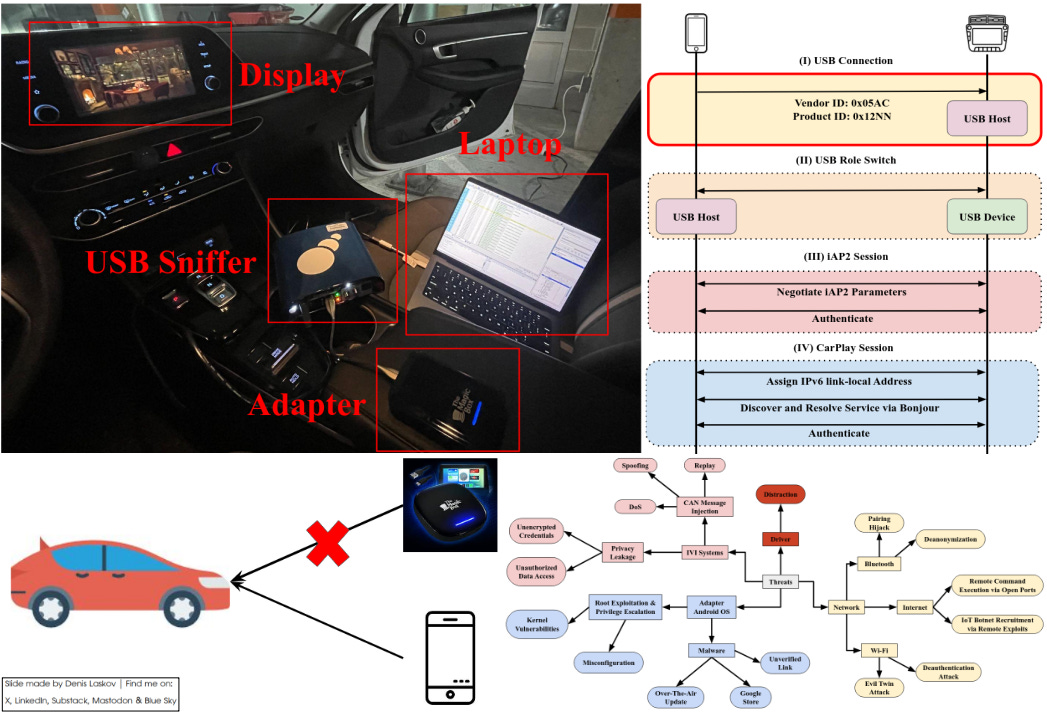
Security issues of third-party CarPlay adapters: from data leaks to CAN message injection. 🚗🔌📱🌐💉🔥
Security researcher Jun Yeon Won and his colleagues share their research on third-party infotainment adapter devices that let older vehicles mimic Apple CarPlay functionality, as well as the security risks these devices pose to the vehicle and its users.
Security or safety risks identified:
🚔 Driver distraction (playing videos or games on the car’s screen while driving)
🚔 Privacy exposure (car and driver data accessible to the adapter and/or the internet)
🚔 CAN message injection (for OBD-II adapters or devices that connect to the CAN bus)
🚔 OS vulnerabilities (mostly Android - privilege escalation, malware installation)
🚔 Wireless attack surface (Wi-Fi, Bluetooth, and internet exposure)
In the tested adapter, while the iPhone believes it’s safely connected to CarPlay, it’s actually interacting with a tiny Android computer pretending to be an iPhone! Impressive.
More details:
CarPlay at Risk: Unveiling Security Threats of Third-Party Infotainment Adapters
Slides [PDF] https://www.usenix.org/sites/default/files/conference/protected-files/vehiclesec25_slides_won.pdf
Presentation [Youtube]: https://lnkd.in/dT6GuB_5