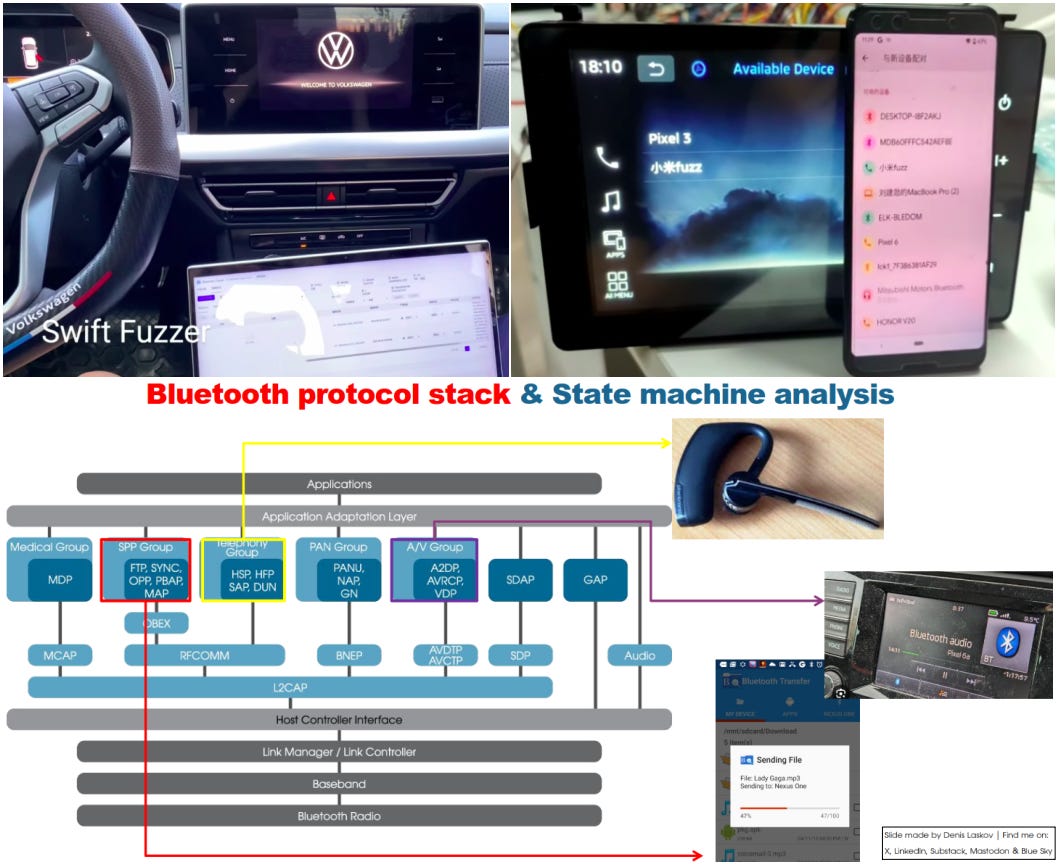
New way to hack Bluetooth in cars: Breaking and reconstructing protocol state machines.🔵🦷🫨🪲😈
Security researchers Lidong Li, Kun Dong, and Xiao Wang presented a new way of finding vulnerabilities in automotive Bluetooth this summer - intentionally disrupting normal Bluetooth protocol flows to expose hidden logic bugs.
For example:
1️⃣ Flooding repeated configuration requests causes driver-level crashes and even system-wide crashes on phones.
2️⃣ High-rate GetPlayStatus requests sent just before timeout cause infotainment systems in cars (Volkswagen) to crash while the vehicle is running.
3️⃣ Repeated SABM frames trigger Bluetooth reset loops, demonstrated on Tesla’s IVI.
4️⃣ Sending SSP pairing confirmation messages too early breaks pairing logic and causes a DoS or state-machine mismatch, demonstrated on Mitsubishi car systems.
And a super useful tip for researchers: Even though Bluetooth security protocols look strict on paper, many Bluetooth interactions don’t require pairing at all. That means a car’s infotainment system can sometimes be crashed (or worse) just by being within Bluetooth range - without any user interaction.
Fun, right? :)
More details:
Unveiling New Attack Vectors in Bluetooth Vulnerability Discovery through Protocol State Machine
Slides [PDF]: https://i.blackhat.com/Asia-25/Asia-25-Li-State-Manipulation.pdf
Presentation [Youtube]: https://lnkd.in/dPVdNgRq