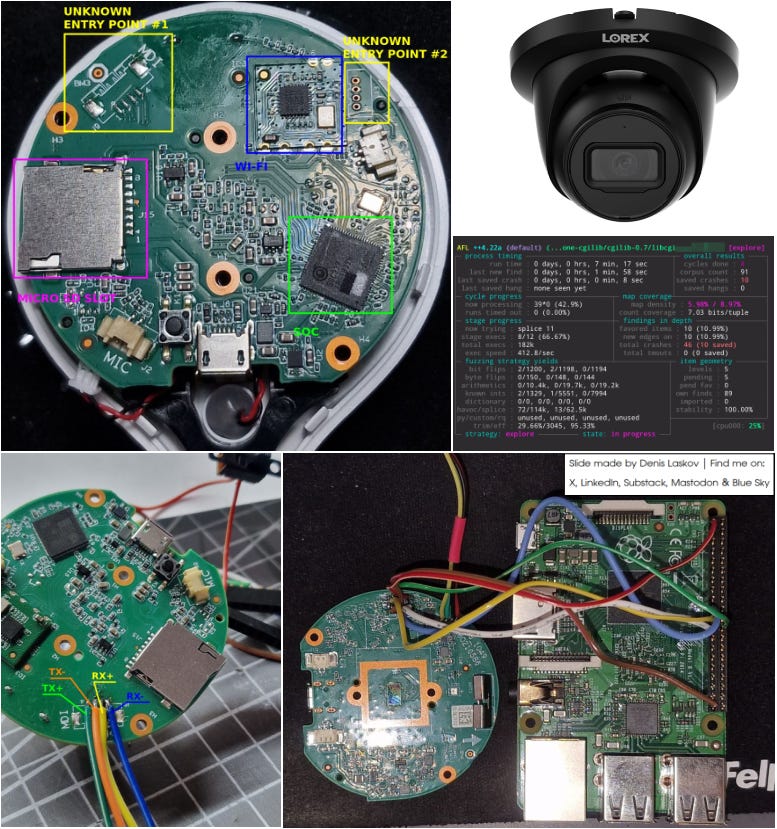
Looking for vulnerabilities in a Wi-Fi security camera: from hardware to fuzzing and back. 👨🏻💻📸🛜𓇲🫨
Security researcher Alessandro Groppo and his colleagues shared a series of blog posts detailing their research on the Lorex 2K Indoor Wi-Fi Security Camera. And even though the result was not a Remote Code Execution (RCE) vulnerability, the research itself is still very interesting!
One of the cool features of this particular series is the retrospective the authors share, which helps them - and us - understand what went well and which parts of the research were mistakes or took longer than they should have.
Double profit from one read: the experience in cybersecurity research and the experience of doing a lessons-learned review to understand the points for improvement.
Enjoy the read, and don’t forget to share!
More details:
Not All Roads Lead to PWN2OWN: Hardware Hacking
Part 1 - Hardware Hacking [Blog]: https://1day.dev/notes/Not-All-Roads-Lead-to-PWN2OWN-Hardware-Hacking-Part-1/
Part 2 - Firmware Reverse Engineering [Blog]: https://1day.dev/notes/Not-All-Roads-Lead-to-PWN2OWN-Firmware-Reverse-Engineering-Part-2/
Part 3 - CGI Fuzzing, AFL and ASAN [Blog]: https://1day.dev/notes/Not-All-Roads-Lead-to-PWN2OWN-CGI-Fuzzing-AFL-and-ASAN-Part-3/