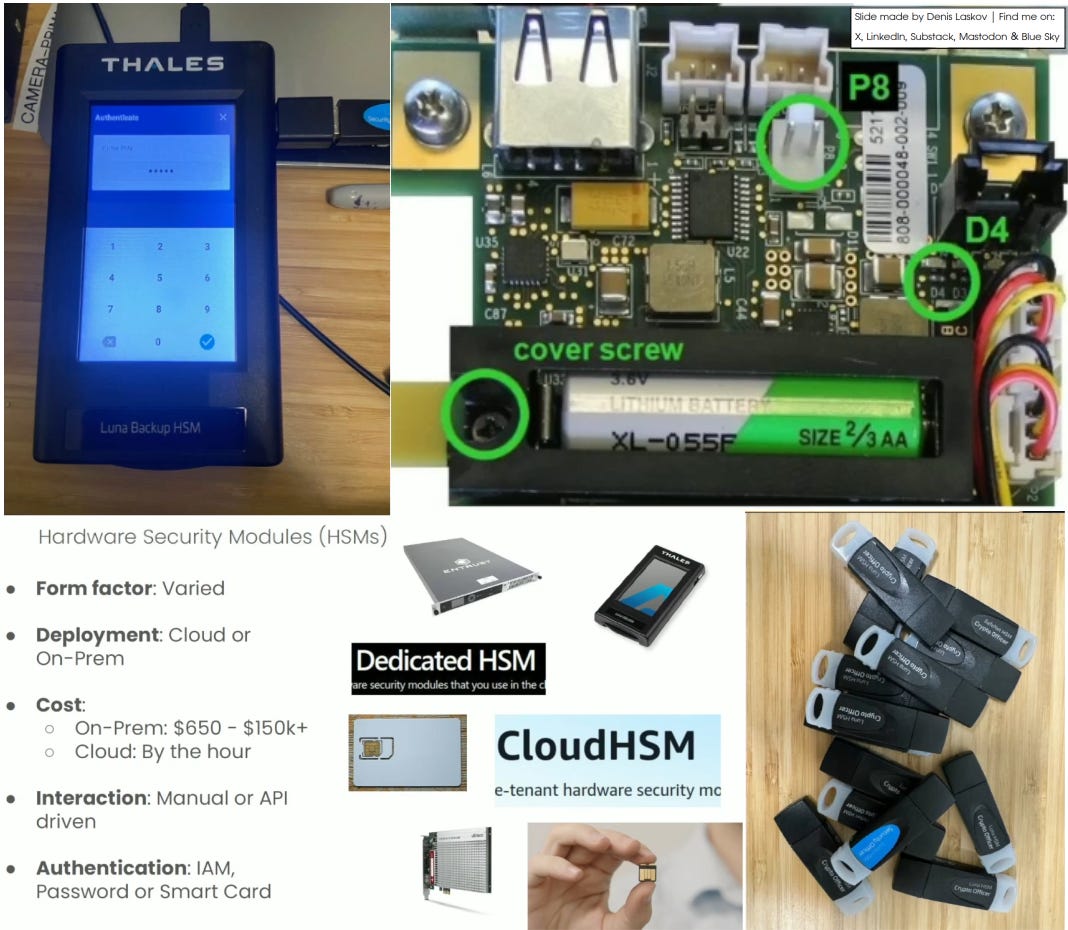
Hardware Security Modules: why to use them, how they work, and tips on how they can be hacked. 📟🗜️🩻🔎🎰
Security researcher and embedded hacker Nick Pelis shares real-world lessons from managing cryptographic keys, especially the “hard mode” cases where keys must live for years or decades. One way to handle this is by using Hardware Security Modules (HSMs).
The stories the author shares from his experience are not only fun and interesting, but also highlight some security issues with HSMs that may come in handy for an attacker:
1️⃣ Operational complexity of using HSMs (key ceremonies, multiple roles, quorum rules)
2️⃣ Human errors (of course!): forgotten PINs, overwritten smart cards, lost recovery tokens
3️⃣ Physical fragility: battery-backed memory, tamper triggers, and “one mistake wipes everything”
Especially fun was learning that some expensive HSM solutions still rely on battery-backed RAM and require a separate protocol and specialized equipment just to change the battery.
Just a friendly reminder that HSMs can be found in PCI (Payment Card Industry), banking (especially interbank communication), military technology, and modern cars.
A great talk for the weekend - strongly recommended! And don’t forget to share. Thanks!
More details:
Care and Feeding of HSMs: Key Management in Hard Mode [Youtube]: https://lnkd.in/dW3K8RTJ