Hacking Unitree humanoid robots: gaining remote control via any available protocol. 👨🏻💻💉❯❯❯🤖☠️
Security researchers Shipei Qu, Zikai Xu, and Xuangan Xiao presented their research on modern humanoid robots this week. Using the Unitree G1 humanoid robot, they demonstrated an end-to-end compromise across every layer of the system:
🤖 Radio control takeover - By reverse-engineering the signal (without firmware access), the team was able to control robots they didn’t own, even when the original controller was turned off.
🤖 App & network attacks - Bluetooth command injection, WebRTC authentication bypass, and MQTT authentication that used passwords derived directly from the robot’s serial number.
🤖 AI assistant exploitation - The robot’s voice assistant used eval() on AI-generated input. With prompt injection or API redirection, attackers achieved remote code execution via the AI itself.
Be very careful near those robots now, because not all these can be patched, vendor says. :)
More details:
Skynet Starter Kit: From Embodied AI Jailbreak to Remote Takeover of Humanoid Robots [Youtube]: https://lnkd.in/dsuPEQMp


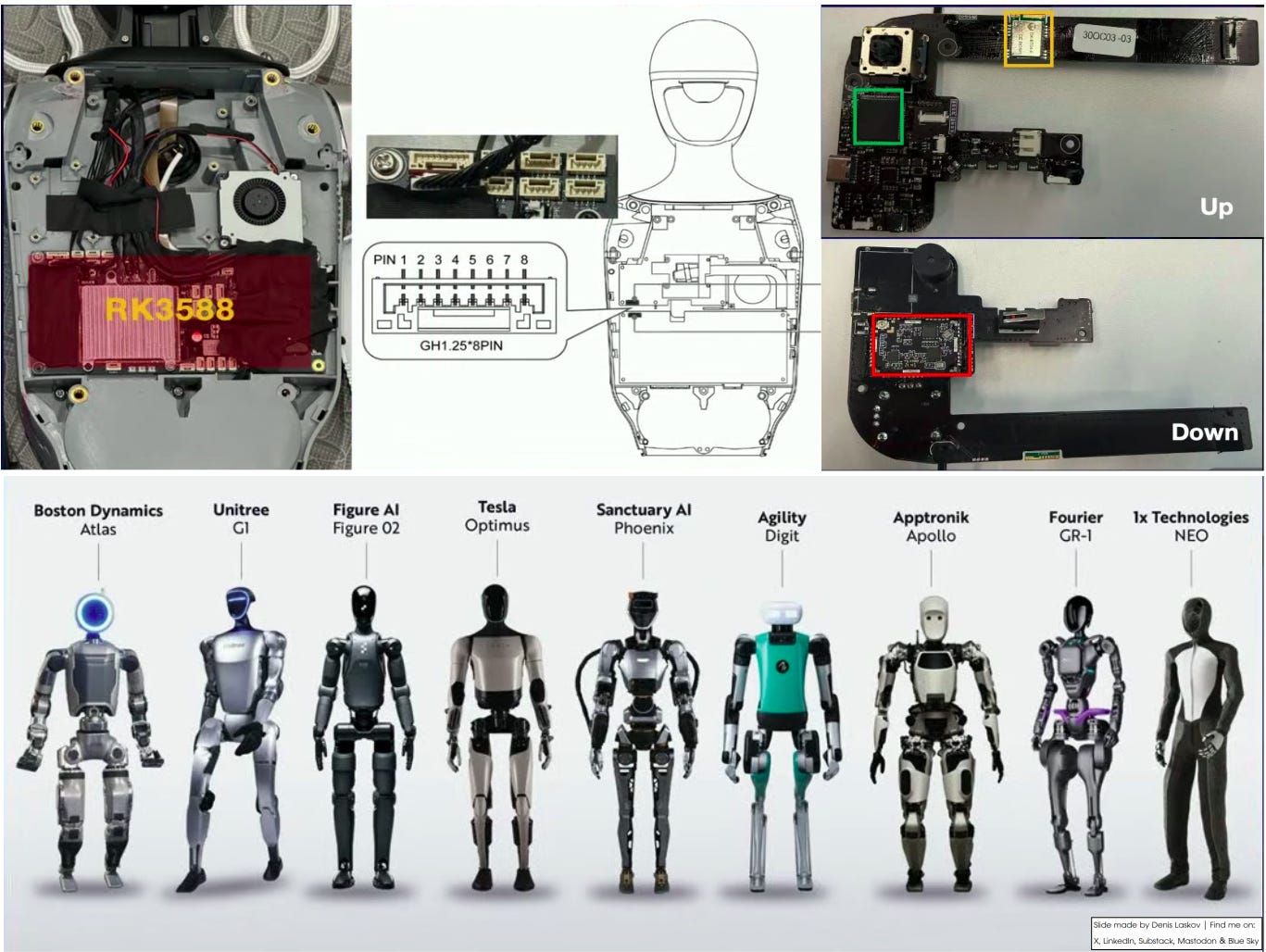
Crazy how much the attack surface expands when you start layering protocols. The serial number derived password thing is wild tho, like it's almost too obvious once you see it. In my exprience with embedded systems, manufacturers still treat authentication like an afterthought and this is a textbook example of that mindset breaking down in production.