Hacking smart TVs via the HbbTV protocol: injecting URLs through unencrypted broadcasts. 📺🧠၊|၊😈🧟
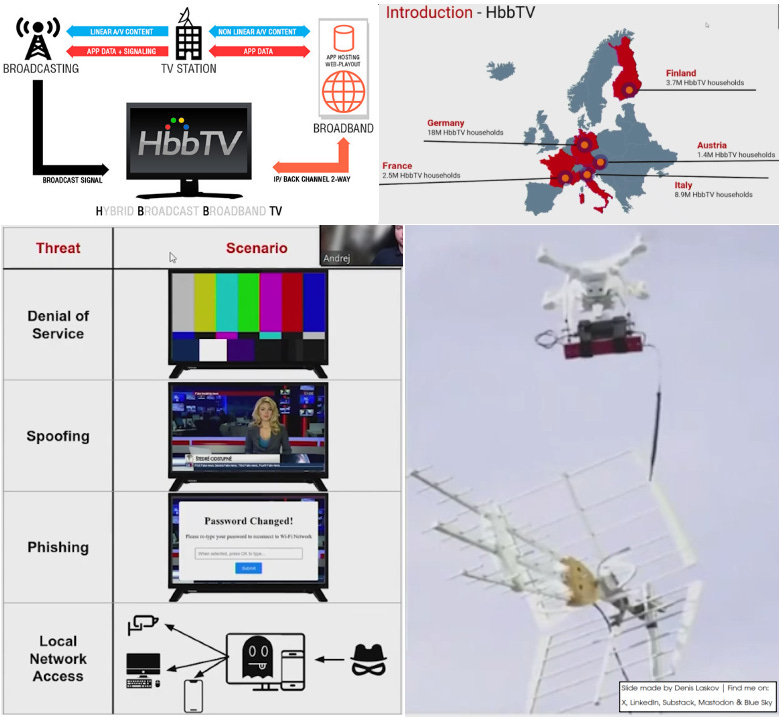
Security researcher Andrej Danis shared his research on smart TVs last month; it focuses on security vulnerabilities in HbbTV (Hybrid Broadcast Broadband TV). The protocol is widely used in Europe and Australia, with millions of devices deployed.
The problem is that the HbbTV client on the TV receives URLs that are transmitted unencrypted within the broadcast stream - meaning attackers can replace them with malicious links.
Author tested 3 TV models,
📺 Toshiba Android TV (2021) – Chrome 55 (from 2016)
📺 Samsung Smart TV (2017) – Chrome 44–55 (from 2014-2016)
📺 LG Smart TV (2024) – Chrome 94 (from 2021)
But wait! The author found that the HbbTV standard relies on web technologies that are deliberately not up to date (for compatibility reasons). I found confirmation of this in the official documentation - see the attached official slides, slide 9.
In other words, does it mean my brand-new “smart” TV is guaranteed to be three years behind in browser security - by design? Interesting.
More details:
Exploiting Smart TVs using the HbbTV Protocol
Presentation [Youtube]: https://lnkd.in/dKHRZ78G
Research paper [PDF]: https://repositum.tuwien.at/bitstream/20.500.12708/213395/1/Danis%20Andrej%20-%202025%20-%20Exploiting%20Smart%20TVs%20using%20the%20HbbTV%20Protocol.pdf
Official HbbTV 2.0.3 Explained [PDF]: https://www.hbbtv.org/wp-content/uploads/2020/12/HbbTV-203-webinar-2020-11-23.pdf