Hacking modern ARM processors: Practical side-channel attacks on Cortex-A72 to recover AES. 👨🏻💻🧲👂📟🔗
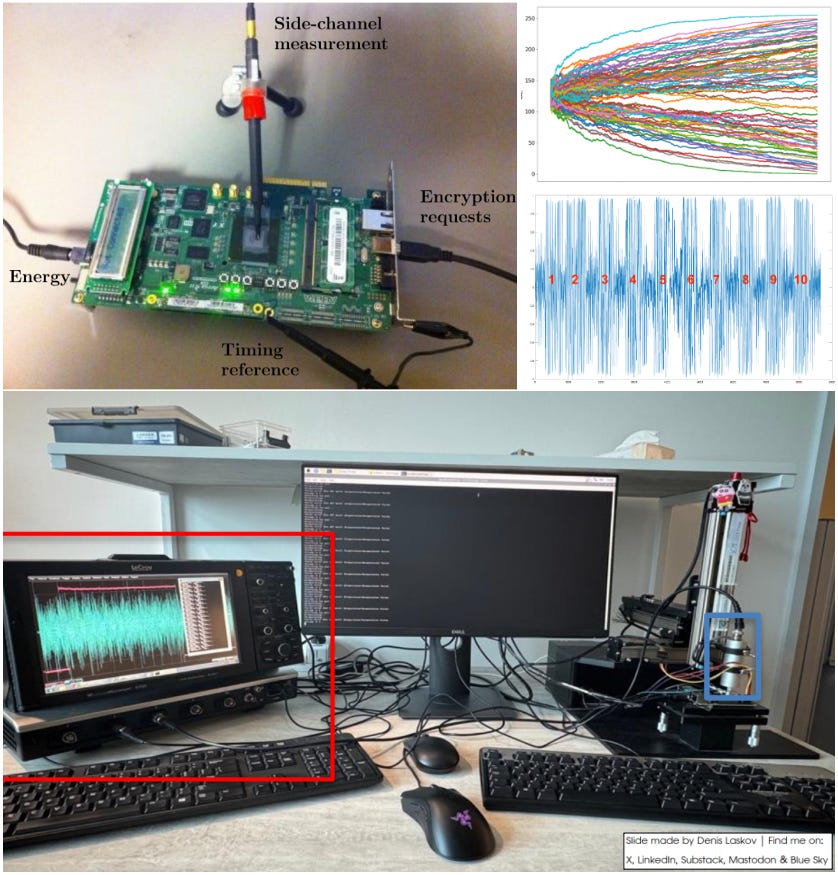
A group of academic and industry security researchers from Singapore share their attempt to answer the following question: How much effort and expertise are needed to extract AES encryption keys from a high-performance ARM processor?
This is one of those papers that not only shares its successes - both theoretical and practical - but also the failures encountered along the way. As the authors mention, it is the first detailed risk-based assessment of AES on an out-of-order ARM core, providing realistic data for designers to plan security defenses.
If you work in security architecture or security engineering for ARM processors, this research may be very practical for you. And if you know someone who does, please share it with them!
More details:
Reality Check on Side-Channels: Lessons learnt from breaking AES on ARM Cortex-A72 processor with Out-of-Order Execution
Slides [PDF]: https://www.usenix.org/sites/default/files/conference/protected-files/woot25_slides_jap.pdf
Paper [PDF]: https://www.usenix.org/system/files/woot25-boyapally.pdf