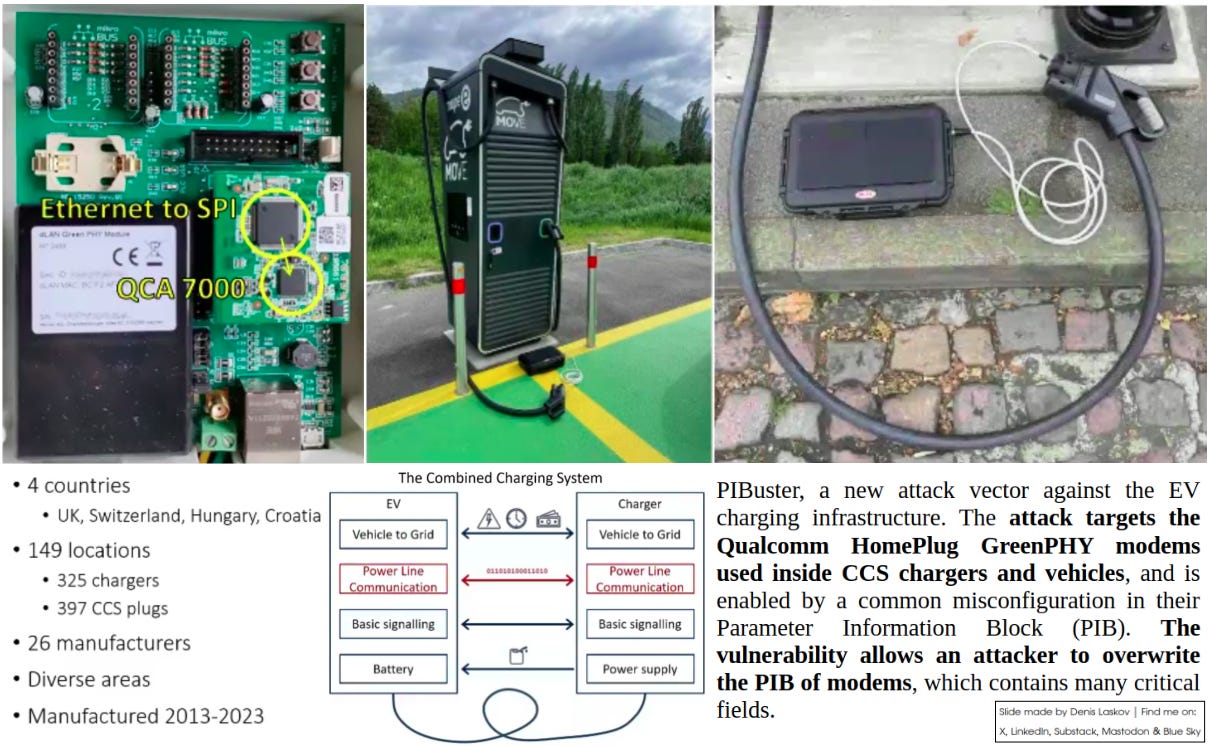
Hacking EV chargers by attacking Qualcomm modems: 41 out of 69 tested chargers are affected. 🚘⛽⚡🪤👩🏻💻
Security researchers Marcell Szakály, Sebastian Köhler, and Ivan Martinovic shared their research earlier this year on EV chargers in Europe and the U.S., revealing a new type of attack on a component common to many EV charger brands: Qualcomm HomePlug GreenPHY modems.
According to the research, 41 out of 69 EV chargers have a vulnerable configuration in the Parameter Information Block (PIB) of the HomePlug modem, which allows an attacker to literally brick the EV charger.
The authors were able to run Doom on a Qualcomm GreenPHY modem by exploiting this vulnerability. Therefore, I assume that this vulnerability could be weaponized by reconfiguring an EV charger into a malicious station that could infect or otherwise damage the car.
Good and solid research, with many interesting insights and significant real-world impact. Strongly recommended reading - please share it with your peers!
More details:
PIBuster: Exploiting a Common Misconfiguration in CCS EV Chargers
Paper [PDF]: https://www.usenix.org/system/files/vehiclesec25-szakaly.pdf
Presentation [Youtube]: https://lnkd.in/damBWKn6