Hacking an Emergency Alert System to fake an earthquake: Stop a city with a single packet. 👨🏻💻♒🚨🫨🫨
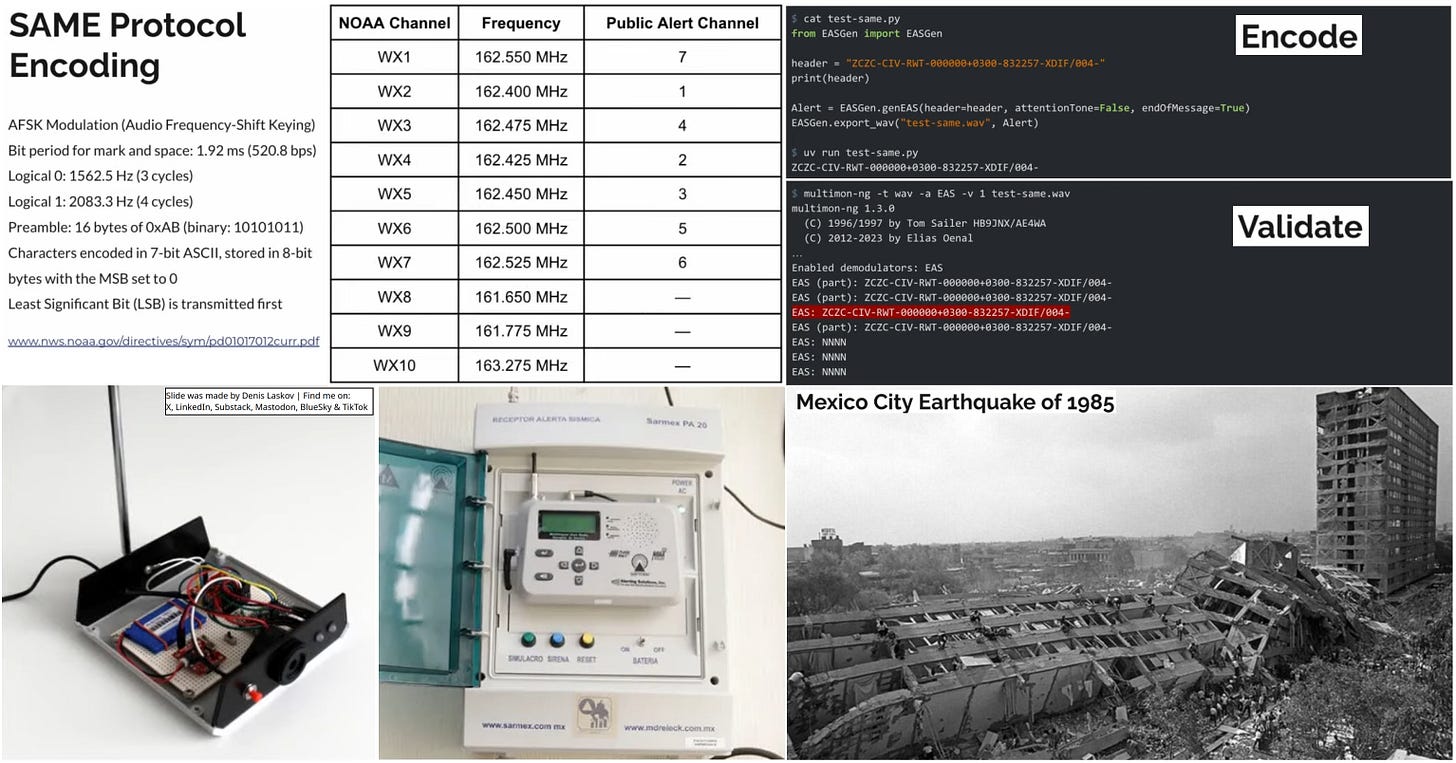
Security researcher Manuel Rábade presented his research last month on how earthquake early warning systems work in Mexico and their use of radio-based emergency broadcasts, especially the Emergency Alert System (EAS) and its SAME (Specific Area Message Encoding) protocol.
EAS and SAME are public alerting technologies that broadcast short digital bursts over VHF, triggering emergency messages on millions of receivers across North America to warn about earthquakes.
The speaker explores the system from an attacker’s perspective - decoding and generating alerts using software-defined radios (SDR) and testing them in a controlled environment. It clearly shows how easy it is to trigger the alerting system and put an entire city into panic.
This is a very rare research topic with huge impact and a very low entry barrier for an attacker. Apparently, these systems have minimal security—perhaps we should spend some budget there.
Please share this research with relevant people if you have them among your friends and colleagues.
More details:
The Small Packet of Bits That Can Save (or Destabilize) a City [Youtube]: https://lnkd.in/dzS9FYkJ


Critical infrastructure security research like this deserves much more attention. The fact that EAS/SAME protocols have such minimal authentication mechanisms is a concerning legacy of an era when physical access was assumed to be a sufficient barrier.
The low entry cost for an attacker (just an SDR) combined with the massive potential impact (city-wide panic) creates an asymmetric risk profile that emergency management agencies need to address urgently. This is especially relevant as SDRs become more accessible and affordable.
Would be interesting to see follow-up research on potential mitigations that could be retrofitted without requiring a complete protocol overhaul.