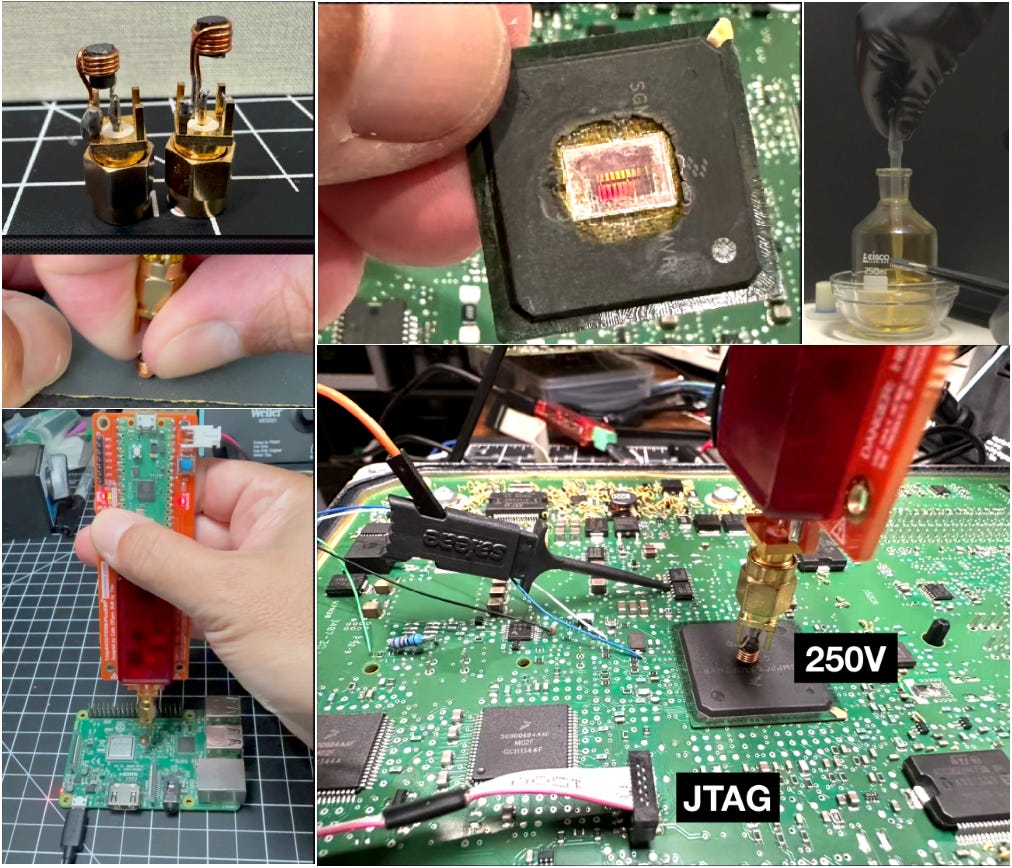
Hacking an ECU from an undisclosed (maybe your?) car: Using glitching to extract MPC5566 firmware via CAN. 🥷🏻🫨🚗🔐
Security researcher Hash Salehi shares the story of a complex reverse engineering job that turned into a two-month technical and emotional roller coaster involving UART and CAN bus hacking, hardware glitching, and writing custom bootloader code from scratch.
Apart from the huge amount of technical detail you're sure to find interesting, there are two messages I want to highlight - and fully agree with:
1️⃣ Academic papers may derail real-world projects because they "forget" to mention critical details. Sometimes, a research paper requires additional research just to understand it. Be careful when planning your projects based on someone else's work.
2️⃣ Emotional toll and determination played a huge role - yes! This is why I strongly recommend working in a group (or having a friend who shares your passion).
🚗 If you work in the automotive industry, the MPC5566 is quite popular in ECUs from many manufacturers for engine and transmission control systems. So - it's safety-relevant. FYI.
Please enjoy the read - and feel free to share it with your colleagues and peers!
Thank you! :)
More details:
BAM BAM on a Budget: You CAN Do It!
Slides [PDF]: https://hardwear.io/usa-2025/presentation/bam-bam-on-a-budget.pdf
Video [Youtube]: https://lnkd.in/dN2U8hQM