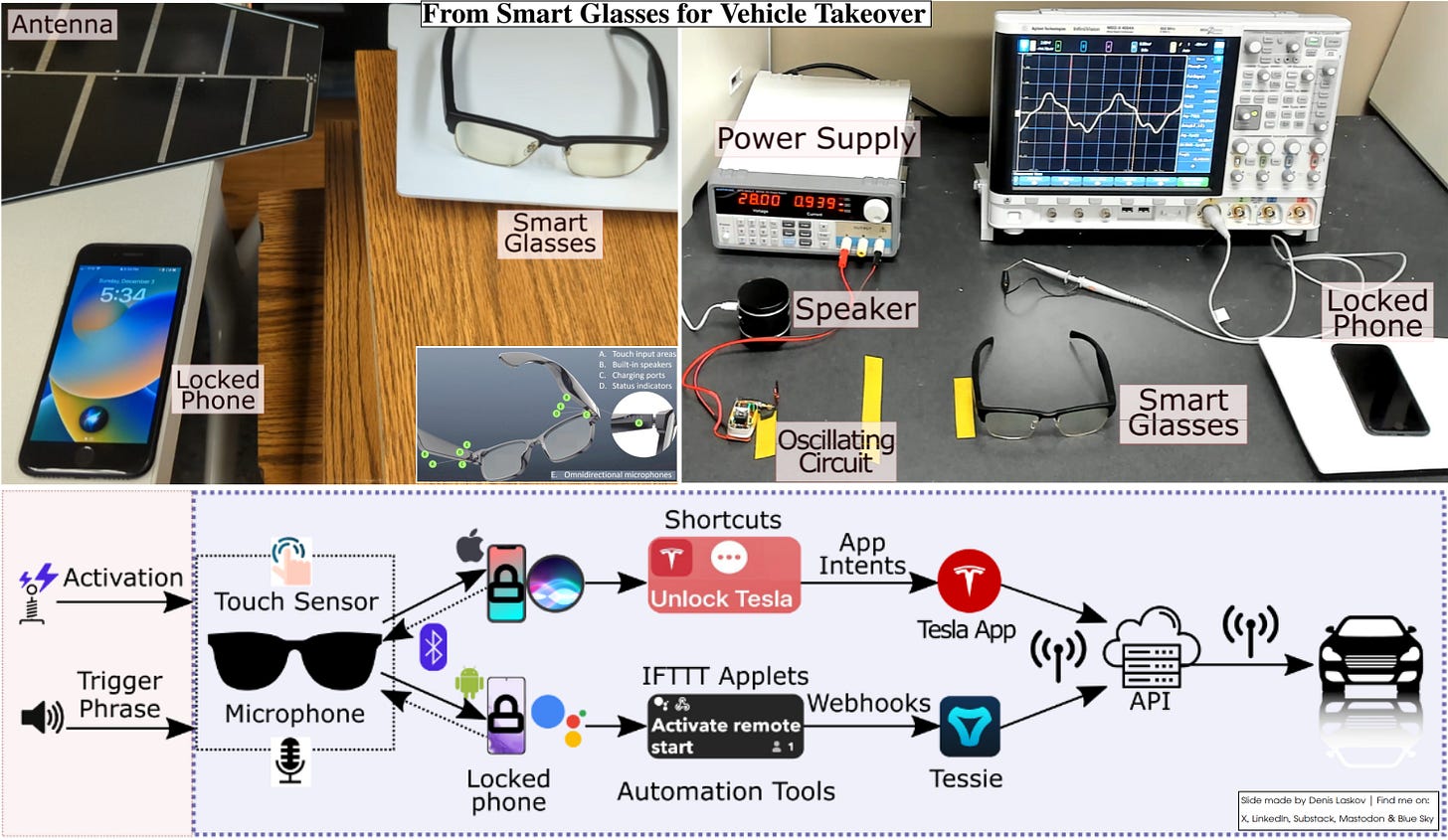
Hack Razer smart glasses first, then steal a Tesla car — a new contactless attack on touch sensors. 🥽❯📱❯🚗🥷🏻
A group of academic security researchers from the US recently shared their research on automated control systems, showing how a vulnerability at one end (smart glasses) can cause serious breaches at the other (a Tesla car).
The entry point is the Razer Anzu smart glasses. By using electromagnetic interference (EMI), attackers can fake touch inputs on the capacitive sensors, activating a paired phone’s voice assistant without physical contact, user interaction, or voice authentication.
Now, using the voice assistant, an attacker can inject commands into all other applications and APIs used by the same phone. In this case - unlocking doors, opening trunks, disabling Sentry Mode, or remotely starting a Tesla car (as an example).
If you’re in the automotive industry - update your threat model, and maybe run a TARA for this new attack vector :) And please share it with your colleagues and peers!
More details:
From Virtual Touch to Tesla Command: Unlocking Unauthenticated Control Chains From Smart Glasses for Vehicle Takeover [PDF]: https://zhiqlin.github.io/file/SP24.pdf