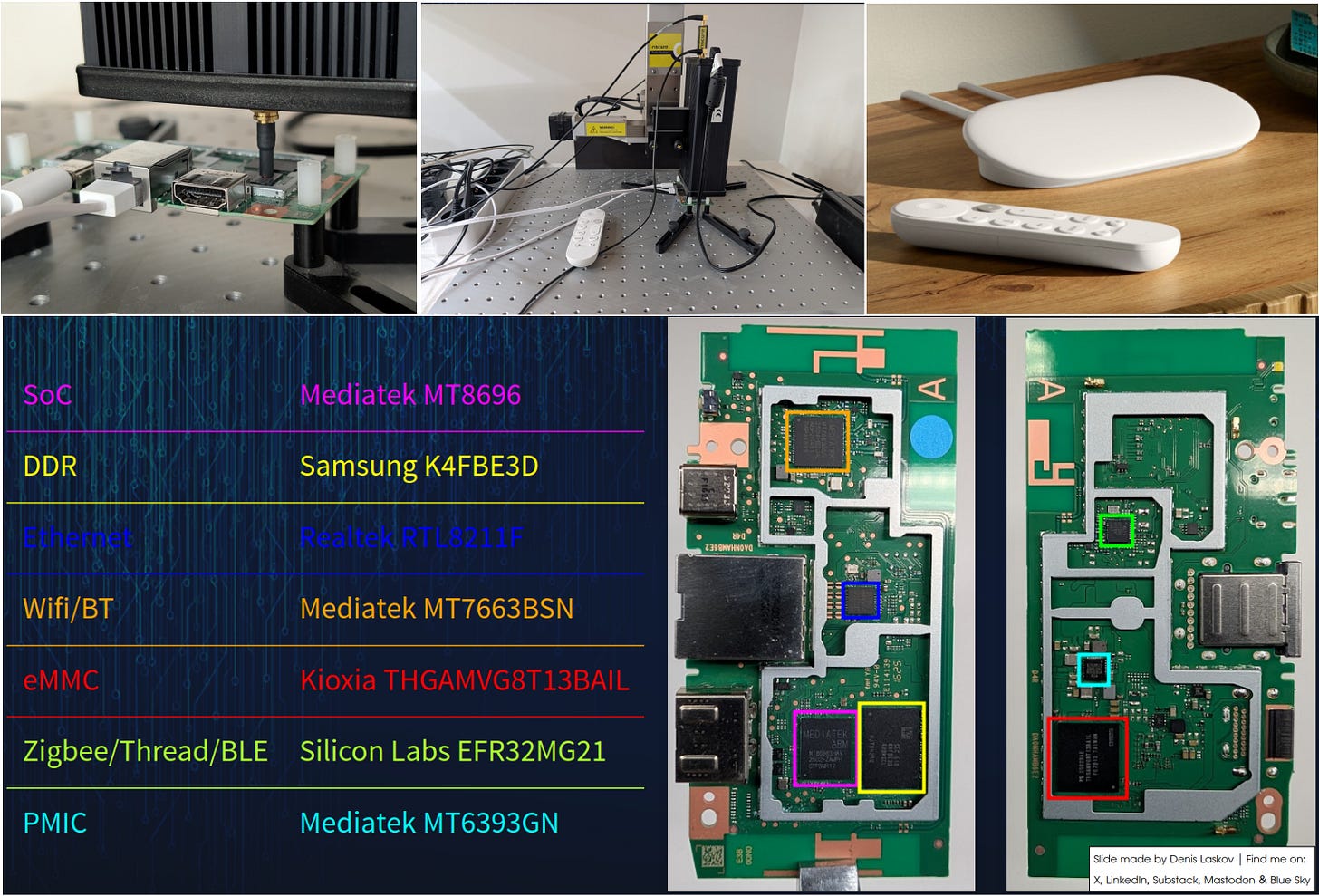
Glitching a Google TV streamer to gain root: successful EM fault injection on a MediaTek chipset. 👨🏻💻⚡📺 🐧>_
Security researcher and fault injection expert Niek Timmers shares another great piece of research on state-of-the-art hardware and ways to hack it using EM (electromagnetic) glitching on an ARM chip.
The author chose to glitch the MediaTek MT8696 while executing the setresuid syscall to change the UID to 0 (i.e., root), then obtained a root shell via Telnet on port 4444. This was successful, but the next challenge is bypassing SELinux using glitching.
A very detailed and well-explained process for attack preparation and execution. And, as usual, impressive results. Looking forward to seeing the second part of this research soon!
More details:
Glitching Google’s TV Streamer from adb to root. [PDF]: https://hardwear.io/netherlands-2025/presentation/Glitching-Googles-TV-Streamer-from-adb-to-root.pdf