Fuzzing 15 commercial cellular basebands: 9 vulnerabilities & honest errors from Google Tensor. 👨🏽🏭❯❯📱🫨🪲
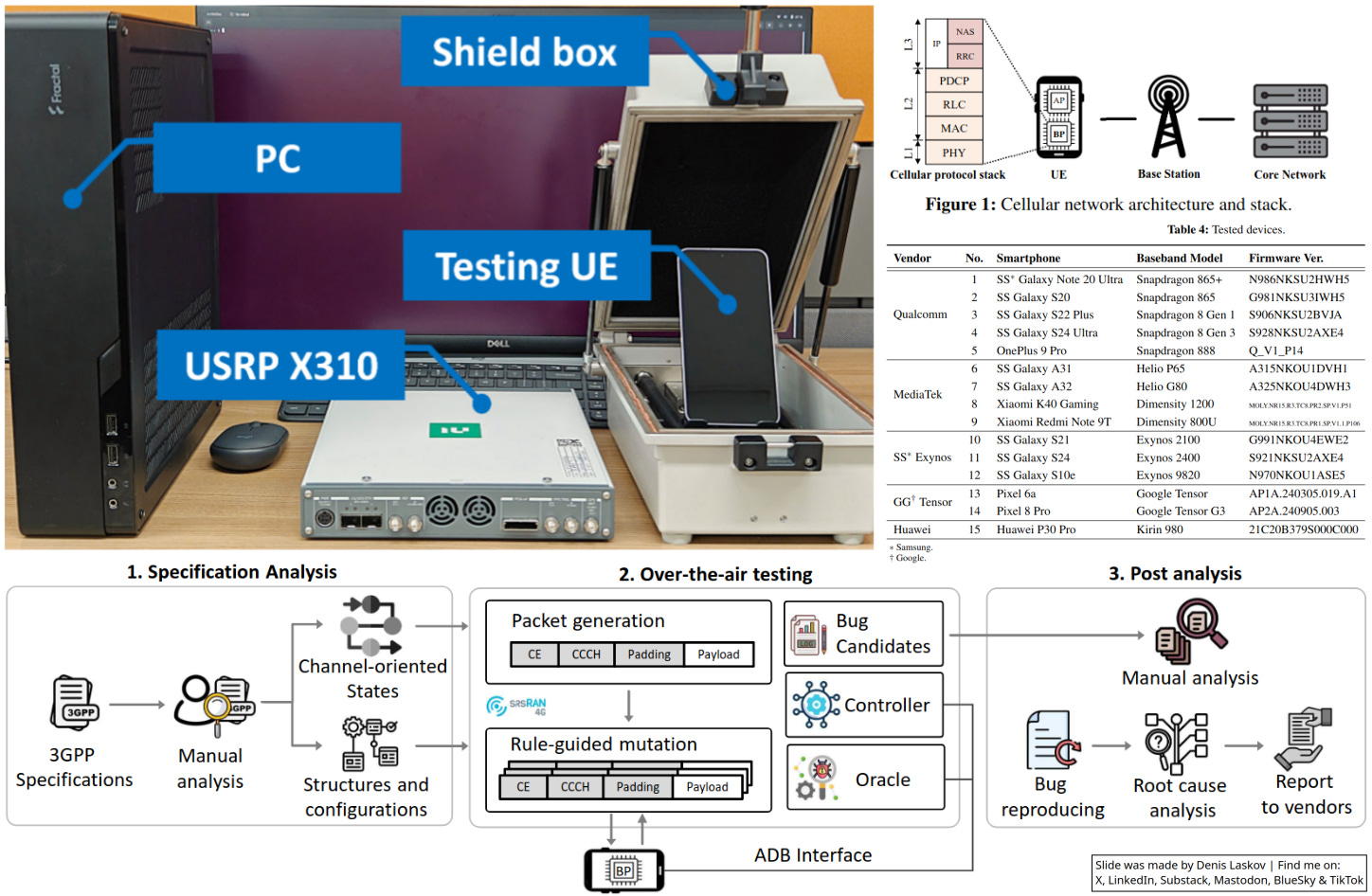
A group of security researchers from South Korea shared a few months ago their work on building lab tooling (hardware and software) to find vulnerabilities in the lower layers of cellular basebands using smart over-the-air fuzzing.
The authors tested their setup on 15 commercial basebands from five vendors (Qualcomm, MediaTek, Samsung, Google Tensor, and Huawei Kirin) and found nine new vulnerabilities so far.
Fun fact: One vendor’s baseband crashes are literally logged as “Everybody panic!” - a unique crash message found only on Google Tensor basebands. That’s probably the most honest error message in telecom history. :)
Authors share their work, including hardware specs, system configurations, and LLFuzz code. So this is a manual on how to approach this kind of research in your lab.
Enjoy and please use it wisely and according to your local regulations!
More details:
LLFuzz: An Over-the-Air Dynamic Testing Framework for Cellular Baseband Lower Layers [PDF]: https://www.usenix.org/system/files/usenixsecurity25-hoang.pdf
LLFuzz [Github]: https://github.com/SysSec-KAIST/LLFuzz