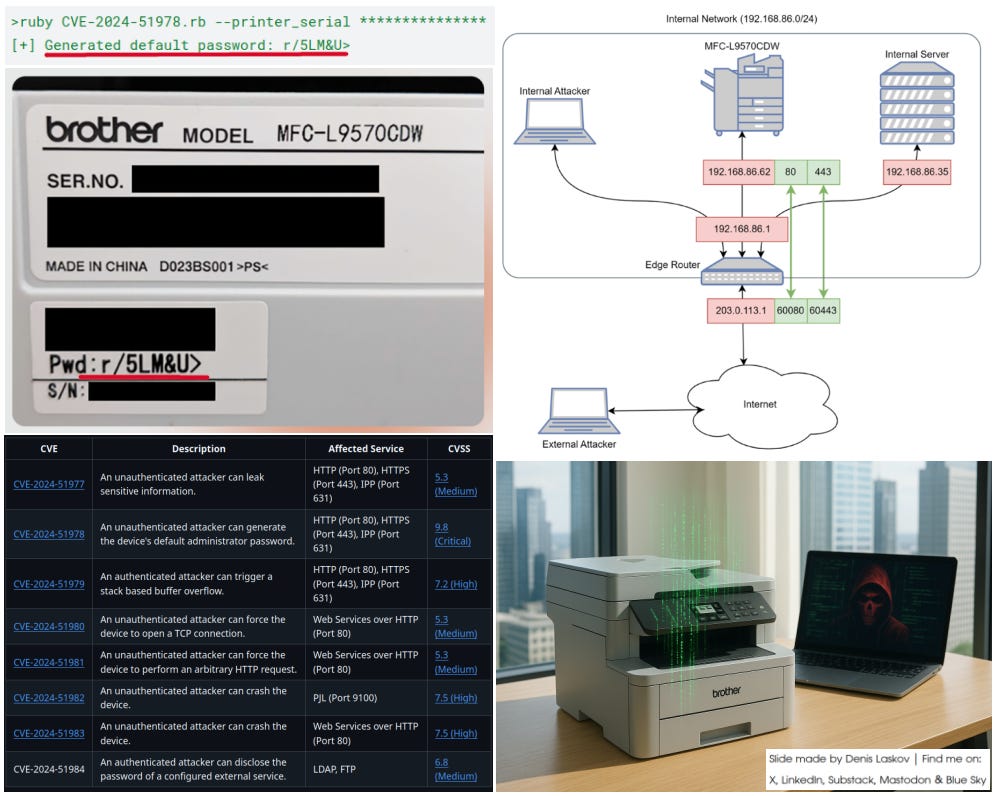
Critical vulnerabilities in 689(!!) Brother printers: predict default password from serial number and more! 👨💻🌐📇🌈👻
Security researcher Stephen Fewer and his colleagues shared extensive research they have been conducting on multi-function printers (MFPs) from Brother Industries, Ltd.
Eight vulnerabilities were discovered and reported to Brother in 2024, fixed by July 2025, and now the technical details plus PoC exploits of all vulnerabilities have been disclosed.
Along with Brother, researchers also tested MFPs and printers from Fujifilm, Ricoh, and Toshiba. In total, 742 models across four vendors were/are affected.
Impressive scale, interesting findings, and a detailed write-up.
Enjoy the details!
More details:
Multiple Brother Devices: Multiple Vulnerabilities (FIXED) [Blog]: https://www.rapid7.com/blog/post/multiple-brother-devices-multiple-vulnerabilities-fixed/
Print Scan Hacks: Identifying multiple vulnerabilities across multiple Brother devices [PDF]: https://assets.contentstack.io/v3/assets/blte4f029e766e6b253/blt6495b3c6adf2867f/685aa980a26c5e2b1026969c/vulnerability-disclosure-whitepaper.pdf
PoC Code in Ruby [Github]: https://github.com/sfewer-r7/BrotherVulnerabilities